In the digital age, your business’s safety hinges on robust anti-virus protection.
Our mission is clear: to arm every business owner with a trusted technical professional, ensuring your venture thrives amidst digital threats.
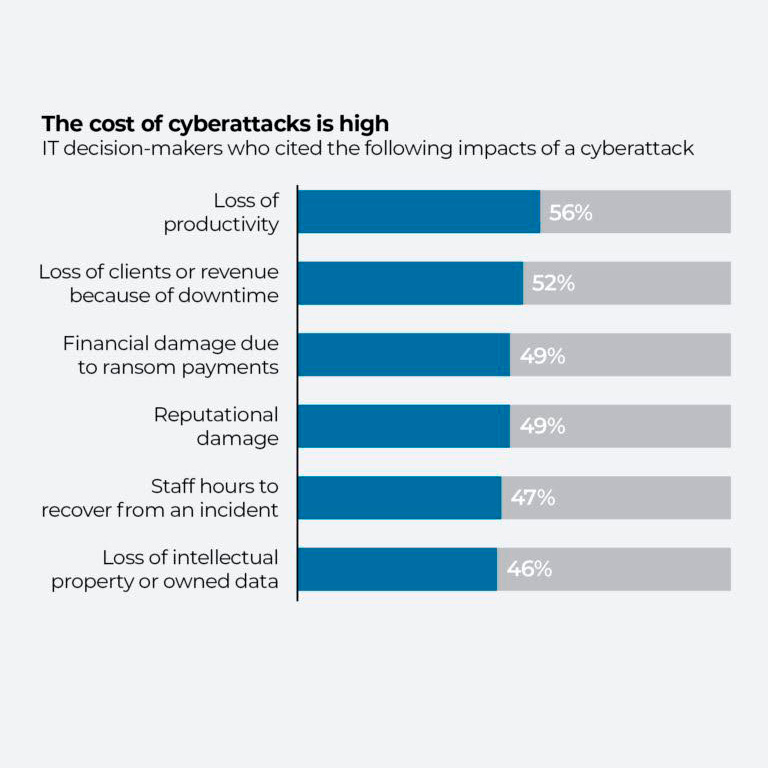
Cyber threats have evolved, becoming more sophisticated and damaging. Annually, thousands of small businesses face significant losses due to cyber-attacks, with viruses and malware leading the charge.
From data breaches to operational disruptions, the cost is not just financial but can deeply affect your brand’s reputation. In this section, we’ll explore the types of digital menaces lurking and share stories of businesses that faced these challenges head-on with our help.
Cyber threats have evolved, becoming more sophisticated and damaging. Annually, thousands of small businesses face significant losses due to cyber-attacks, with viruses and malware leading the charge.
From data breaches to operational disruptions, the cost is not just financial but can deeply affect your brand’s reputation. In this section, we’ll explore the types of digital menaces lurking and share stories of businesses that faced these challenges head-on with our help.
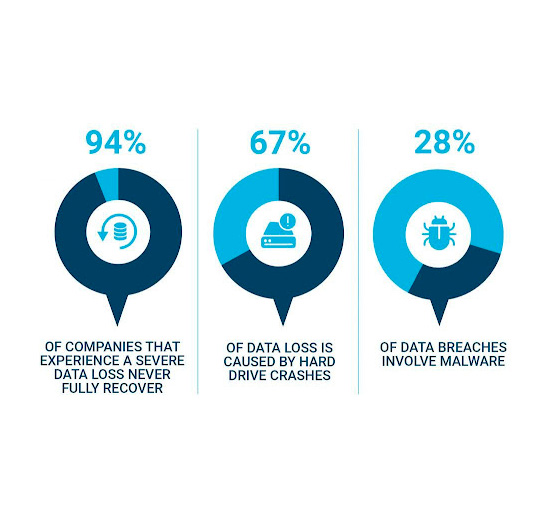
Pro Group Networks provides more than just software; we deliver a service backed by experts committed to your business’s safety because we understand what a cyber attack means to your business.
Our approach includes regular updates and real-time monitoring, ensuring you’re always one step ahead of potential threats.
Pro Group Networks provides more than just software; we deliver a service backed by experts committed to your business’s safety because we understand what a cyber attack means to your business.
Our approach includes regular updates and real-time monitoring, ensuring you’re always one step ahead of potential threats.
Pro Group Networks provides more than just software; we deliver a service backed by experts committed to your business’s safety because we understand what a cyber attack means to your business.
Our approach includes regular updates and real-time monitoring, ensuring you’re always one step ahead of potential threats.

Implementing our anti-virus service is a seamless process designed to minimize disruption.
Initially, our team conducts a thorough assessment of your current systems to tailor the setup.
Following installation, we embark on continuous monitoring and regular updates, key components of our proactive defense strategy.
Here, we’ll walk you through each step, demonstrating our commitment to keeping your business secure without complicating your daily operations.
Initially, our team conducts a thorough assessment of your current systems to tailor the setup.
Following installation, we embark on continuous monitoring and regular updates, key components of our proactive defense strategy.
Here, we’ll walk you through each step, demonstrating our commitment to keeping your business secure without complicating your daily operations.
Understanding whether your business is at risk of a virus infection starts with recognizing the multifaceted nature of cyber threats. Virtually every business, regardless of size or industry, faces some level of risk, primarily due to the increasing sophistication of cyber attackers and the expanding attack surface in our digitally connected world. Here are several factors that can elevate your risk:
To mitigate these risks, conducting regular security audits, investing in comprehensive cybersecurity solutions, and fostering a culture of cyber awareness among employees are critical steps.
A virus infection can manifest through various signs, some subtle and others quite disruptive. Recognizing these signs early can be crucial in preventing significant damage to your systems and data. Here are key indicators:
Monitoring your IT infrastructure for these signs and having a proactive response plan are essential for maintaining your cybersecurity posture.
Acting swiftly and methodically is crucial when you suspect a virus infection. Here’s a step-by-step approach:
Regularly updating your incident response plan and conducting cybersecurity drills can prepare your team to act effectively under the threat of a virus infection.
While anti-virus protection is essential, true cybersecurity requires a holistic approach.
Pro Group Networks offers a suite of services designed to cover all aspects of your digital defense, from firewalls and ransomware protection to comprehensive security audits.
Discover how our integrated solutions can fortify your business against the full spectrum of digital dangers.
While anti-virus protection is essential, true cybersecurity requires a holistic approach.
Pro Group Networks offers a suite of services designed to cover all aspects of your digital defense, from firewalls and ransomware protection to comprehensive security audits.
Discover how our integrated solutions can fortify your business against the full spectrum of digital dangers.
Pro Group Networks is ready to be your trusted technical ally, ensuring your business remains resilient in the face of digital threats. Call us at (702) 330-3047 or fill out our contact form bellow to learn more about our anti-virus services and how we can help secure your digital landscape.
Are you ready for a better way to work with technology? We break down technology into easy-to-understand language and work with our clients to create solutions so that they can keep running their business smoothly with no interruptions.